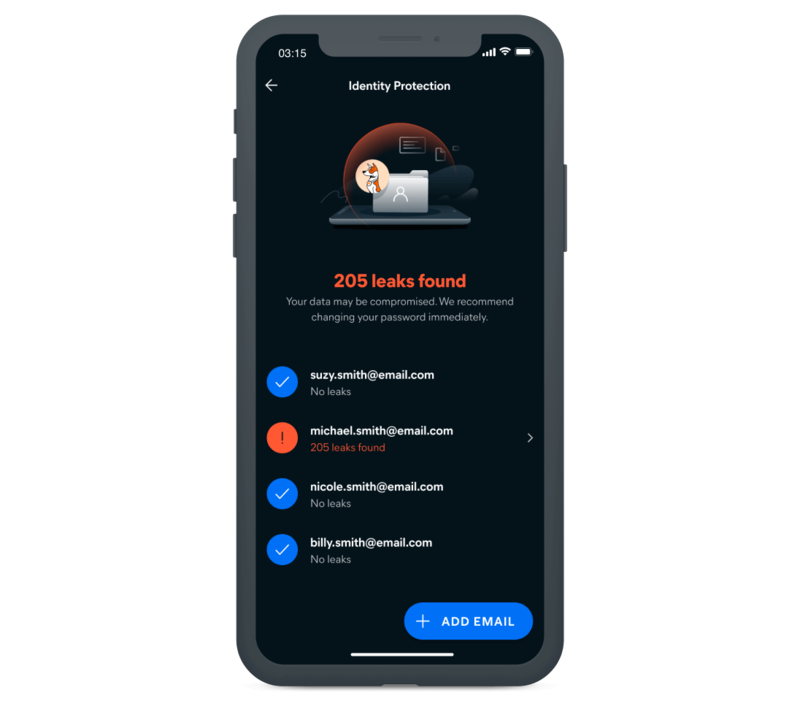
Hand with Smartphone Chatting Security Email Network Social Media Stock Vector - Illustration of business, application: 160671937

Proofpoint Is Named a Leader in The Forrester Wave™: Enterprise Email Security, Q2 2021 | Proofpoint UK

Mobile Device Security: 5 Best Practices to Avoid HIPAA Violations | Columbus, Ohio Healthcare IT – SupportNet