Essential English Skills for the Australian Curriculum Year 8 2nd Edition: A multi-level approach: Amazon.co.uk: Brownhill, Anne-Marie, Rucco, Alison, Stoneman, Sonya, Simpson, Deborah: 9781316607671: Books

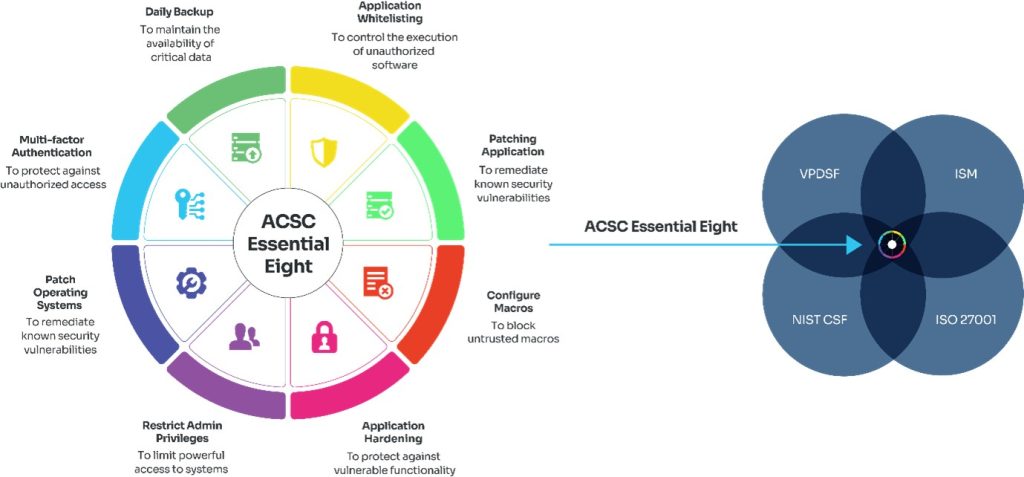
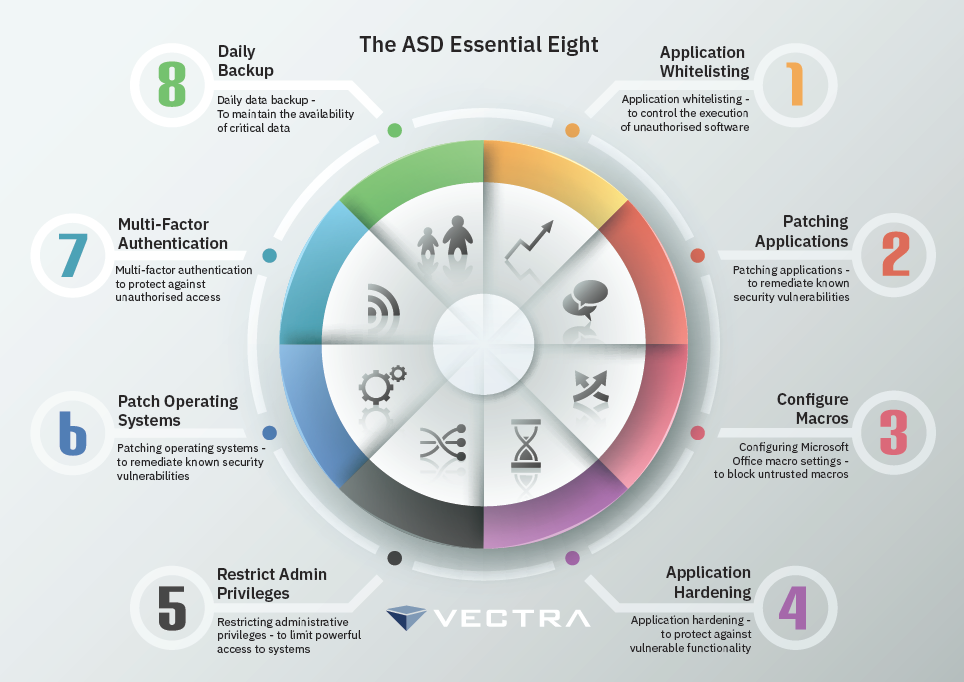
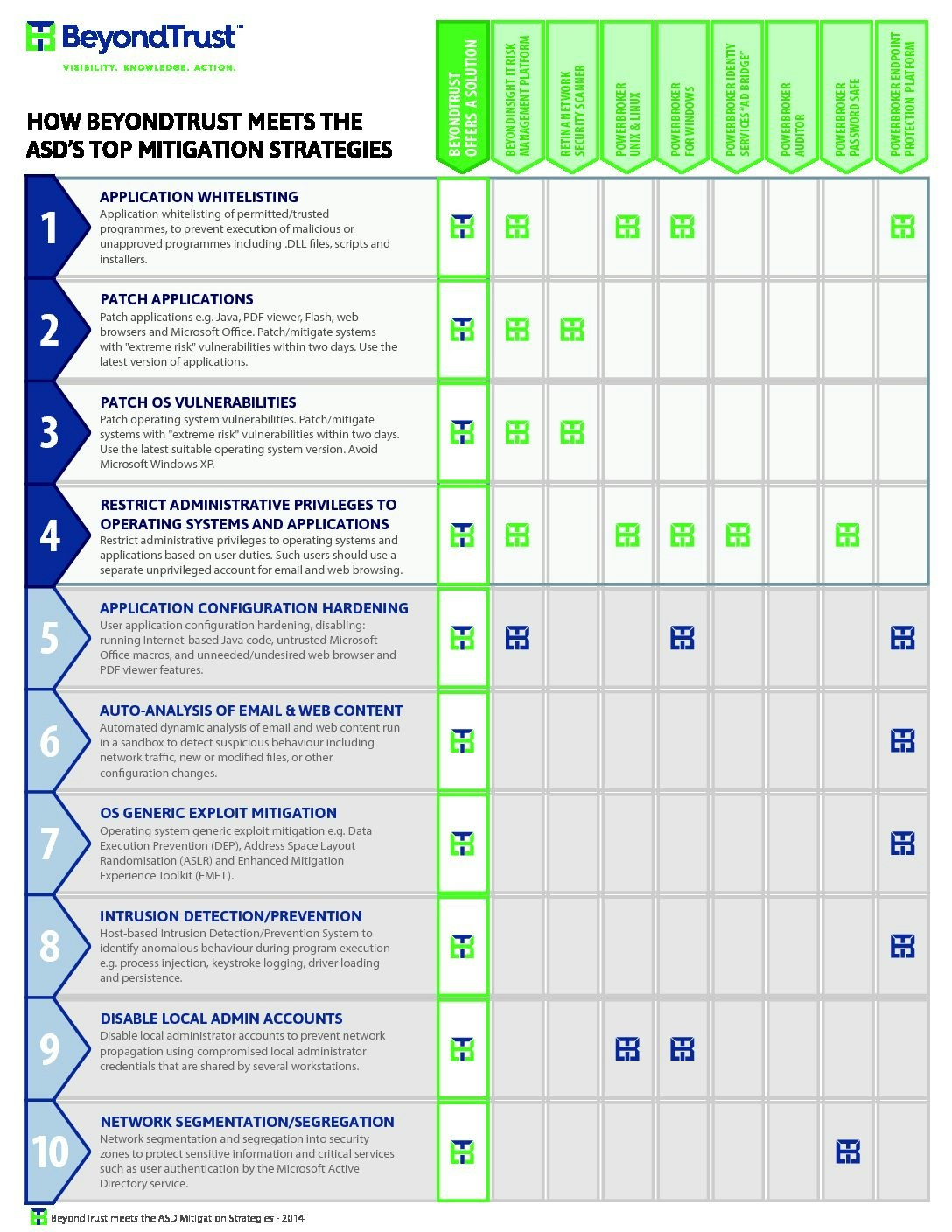
Essential Eight explained: ACSC's key security controls for organizational cybersecurity | Data Security